Cybersecurity So Bad, It Makes You WannaCry
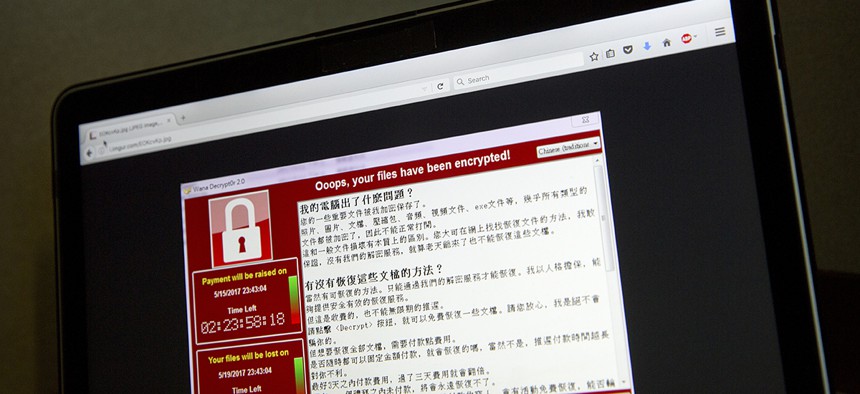
A screenshot of the warning screen from a purported ransomware attack, as captured by a computer user in Taiwan, is seen on laptop in Beijing. Mark Schiefelbein/AP File Photo
There are many interesting elements about the ransomware attack, the biggest being the tools to stop it were readily available.
John Breeden II is an award-winning journalist and reviewer with over 20 years of experience covering technology and government. He is currently the CEO of the Tech Writers Bureau, a group that creates technological thought leadership content for organizations of all sizes. Twitter: @LabGuys
There are so many other topics I wanted to write about this week, like the new cybersecurity executive order, or the fact just a week after my last column on autonomous vehicles, another state is entering the long road toward deploying driverless cars. Gov. Andrew Cuomo announced New York is now accepting applications from companies interested in testing or demonstrating autonomous vehicles on public roads in that state. Moving right to the testing phase is pretty cool, surpassing other states that are still studying the issue. So, if you want to see driverless cars in the near future, I suppose New York is the place to be.
But plans for those columns got put on hold after the global cyberattack named WannaCry, among other monikers, expanded over the weekend. In an event destined to have its own Wiki page and maybe even a feature film, hacking tools stolen by the National Security Agency and published online were used to instigate what could eventually become one of the largest cyberattacks in history. Hackers used the NSA tools to craft a ransomware attack against a British health care system, which then rapidly spread to other companies and countries.
» Get the best federal technology news and ideas delivered right to your inbox. Sign up here.
There are many interesting elements about this attack, the biggest being the tools to stop it were readily available. Microsoft released a patch over a month ago to close the vulnerability WannaCry and the NSA tools exploited, yet it’s apparent many people, organizations and governments didn’t bother to deploy them.
I suspect the attackers never meant for their attack to become a global event. On the surface, other than using the NSA-provided tools, this was a run-of-the-mill ransomware scheme with a defined target and a reasonable demand of $300 per client for payment.
It wasn’t even that sophisticated, using TOR servers for command and control, which can be easily blocked by most enterprise security services or programs. The attackers probably wanted to get a quick payday from their ransomware, collect their money and then anonymously disappear. That they became infamous on the global stage won’t do them any favors.
It’s also interesting to note computers at Russian companies are reportedly being infected now. It’s well-known Russia does not hunt and prosecute most hackers within its borders so long as they don’t attack Russian systems, and especially Russian government systems.
Hackers who want to avoid upsetting their hosts often put code in their malware that keeps it from deploying if the native language on an infected system is set to Russian. In China, it’s not even technically illegal to attack systems outside of the country. So, either the hackers behind this attack are not based in Russia or China, or they never thought it could possibly blow back to them, and thus never bothered to add local safeties into their code.
With WannaCry, we have a hodgepodge of older attack techniques targeted at unpatched systems in a specific health care organization. But instead of a quick bit of extortion and a nice little payday, it instead turned into a global event.
This could only happen in an environment where cybersecurity is such a low priority within most organizations, and even governments, that attackers can’t even target specific groups without their malware spilling out across the globe.
The one silver lining is that as of this writing, no American government agency has reported being infected with WannaCry. Of course, the fact that the stolen tools used in the attack came from NSA doesn’t make us look too good, but at least we seem to be practicing basic cybersecurity.
Going back to that recent executive order on cybersecurity, it could not have come at a better time. While much of the order provides a framework for future improvements, one immediate directive was that, “each agency head shall use The Framework for Improving Critical Infrastructure Cybersecurity ... developed by the National Institute of Standards and Technology, or any successor document, to manage the agency’s cybersecurity risk.”
Some have criticized the framework for being too general about cybersecurity, although it’s being upgraded to version 1.1 to include advice about supply chain risk management, metrics accounting, identity management and access control. Those more advanced concepts, while important, were not required in this case. In an era where a low-level attack like WannaCry can affect, perhaps accidentally, organizations all around the world, a good starting point is exactly what is needed.
For the federal government, the fact that most of its agencies were following the NIST framework, even before the order, probably saved many systems from this most recent threat. The government could still be vulnerable to highly targeted attacks, with quite a few occurring recently, but at least we seem to be protected from the most basic of threats like WannaCry. And that’s a lot better than most organizations.



